Each year a particular standard, component, model or approach within the identity and access management space will be declared “dead” by expert commentators, startup vendors or just the bloke in the pub. As part of The Cyber Hut’s Tuesday polls, I decided to test the water on this highly emotive topic before the Christmas holidays for our last poll of 2022.
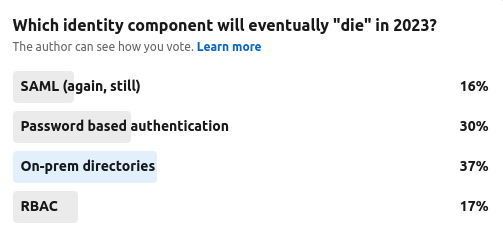
I chose the top 4 most “mature” (legacy / stable / old fashioned / trusted / complex – you decide) topics that can guarantee a good 20 mins worth of discussion out of the most reserved of identity practitioner.
105 people responded and the results were pretty mixed it has to be said. On-prem directories just came out on top, but it was pretty close with password based authentication, with RBAC and SAML the work horses that just wont die coming in a relatively joint 3rd place.
Let’s take a look at each one and provide a rationale for and against.
| For Death | Will See Out 2023 At least | |
| SAML | Based on XML and relatively bulky to implement in code. Meta data management a continual operational issue, with the issue of certificate updates/revocation always an issue. Not as sexy as OAuth2/OIDC for API protection / social federation. | Used ubiquitously and once deployed, stable and performant. Time consuming to migrate away from. Well understood with many products supporting it, especially for cloud single sign on. |
| Passwords | Password breaches are at an all time high. Strong MFA using something I have (key/phone) combined with something I am (mobile biometrics) is becoming common and simple to deploy. See likes of HYPR, 1Kosmos, Secret Double Octopus along with FIDO2/WebAuthn. | Passwords are “free” at the point of deployment – costs come later. They’re also well understood by Joe Bloggs end user. Password managers (for all their breaches too) provide a means to generate site-specific complex passwords, letting them live a little longer yet. |
| On-prem Directories | Costly and notorious for having poor governance, the operational overhead of housing globally dispersed, highly available directories is high. Requires specialist teams and management. Cloud directories and stores are popular (see Azure AD, Okta, ForgeRock, Ping, Jump Cloud et al) which provide relatively cheap and scalable identity repositories. | Cloud directories need to be fed – how do you get good clean identity data inside them? Once populated they do need managing with strong access request and review processes. How to integrate a cloud directory with on-premises systems and workflows? On-prem systems may slow down the migration. |
| RBAC | The constant hum of role explosion, separation of duties violations and the constant compliance process of managing access review reports sees RBAC fall into the “not quite” category as a successful access control concept. Not really seen as practical for anything but the most complex large enterprises. | Alternatives such as attribute based access control (ABAC) suffer from the same governance and hygiene issues and more recent concepts such as relationship based access control (ReBAC) based on graphs is still early in the deployment life cycle. |
