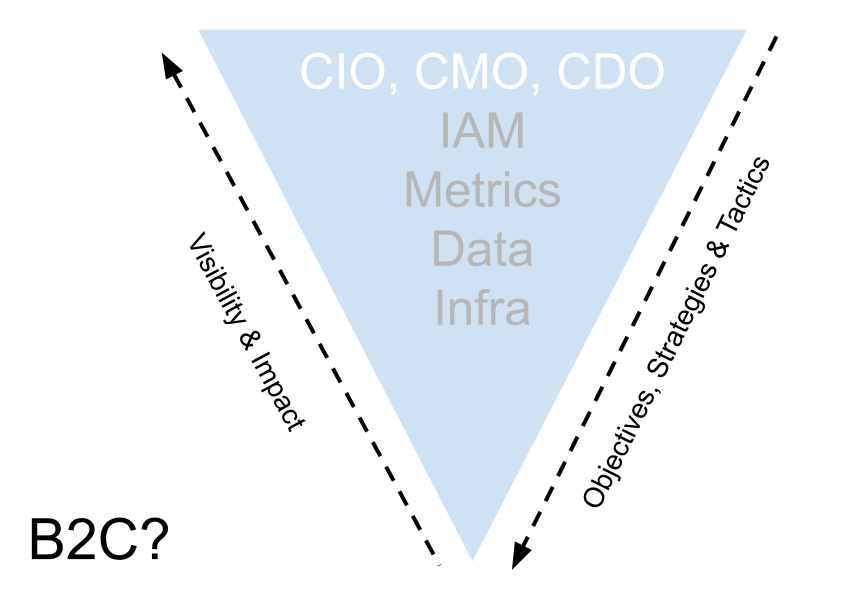
Do we need a "Chief Identity Officer"? What might drive the need for this and can existing business operating models satisfy the need for identity centric metrics?
Some items that have hit The Cyber Hut intelligence inboxes this week. State of Passwordless Authentication […]
Identity and Access Management has long been confined to two (or maybe three) buckets: B2E (employee […]
Join our founder Simon Moffatt on February 15th to understand why zero trust network architectures should […]
On January 26th, the US Government issued a memorandum, relating to the adoption of zero trust […]
A few items that have popped into The Cyber Hut inboxes over the past week relating […]
A few items that have popped into The Cyber Hut inboxes over the past couple weeks […]