I recently ran another of my highly scientific polls on cyber security technology opinions last week that asked the question as to whether passwordless authentication still classified as multi factor authentication (MFA). I dropped the polls into LinkedIn and Twitter here. It generated some interesting responses. Before we dive into that, let me set the scene (again) regarding the different authentication types and what MFA really pertains to and why it’s popular.

Authentication is typically broken down into the three “something you know”, “something you are”, and “something you have” buckets – with MFA selecting two from the three. As the vast majority of people based authentication starts with a username and password, a second factor takes one from something you are (such as a fingerprint or facial recognition) or perhaps a USB security key. The second factor helping to provide a dynamic and out of band component due to the failures of password centric single factor authentication.
So back to the poll. I ran the LinkedIn poll for 7 days (albeit most votes occurred during the first three days). It received 66 votes and had nearly 3000 views and has a couple of days still to run.
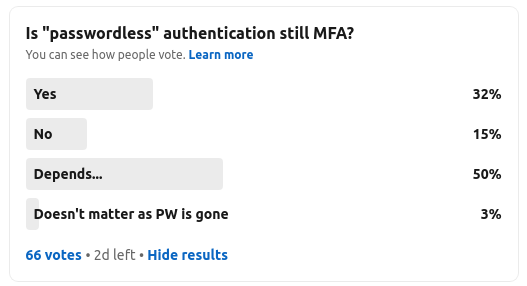
Clearly, the question was vague enough to generate a good 50% of “depends” – top marks for the analytical types out there who wanted to hedge their bets. The question was really to prompt an initial response. 15% of voters thought that passwordless is not MFA. Now clearly, it is possible to design a passwordless authentication solution that is indeed single factor. Perhaps just leveraging an asymmetric key pair in a single channel. However, the majority of commercial passwordless solutions tend to leverage biometry on the device. I wont get into the storage of the biometric template here – some store the biometric template within the device, others in cloud services in distributed storage models, perhaps using block chain or models such as Shamir’s Secret Sharing. The takeaway is that the device is unlocked using biometrics and biometrics are again used during subsequent authentication events.
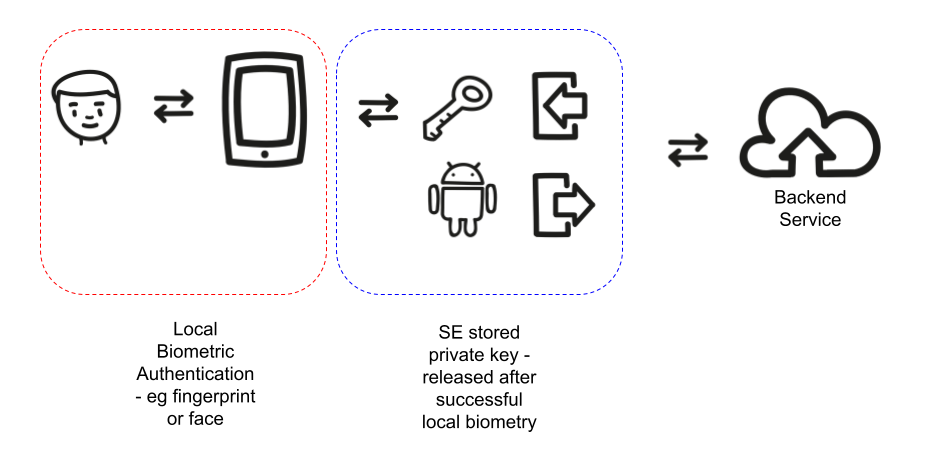
The “subsequent” login event of course can be highly complex – but at a very high level this might well leverage a dynamic challenge response interaction. A back-end service that requires evidence of an authentication event, triggers the process by issuing a challenge – perhaps a random number or number used only once (nonce) to an app running on the mobile. That app interacts with the trusted interface components to capture face pictures or fingerprints which are processed to identify a match to a previously registered user. On successful completion of this step, secure storage on the device can be accessed to access the previously generated private key that can be used to respond to the challenge – perhaps by decrypting the request, or signing a response back, depending on the design.
The point here, is that another decoupled component is at work, separate to the biometric aspect. This essentially brings us to two factors – something the user is, and something they have (which is a trusted device that contains a copy of the private key – the private key may have been derived and re-computed on the device too).
But the question remains – why do 15% of the highly unscientific poll think passwordless is not using MFA? Perhaps marketing, perhaps unfamiliarity. I would imagine that is clearly a barrier to adoption though for passwordless technology.
The Twitter poll was similar, albeit slightly more opinionated. 11 people responded on a 3 day poll.
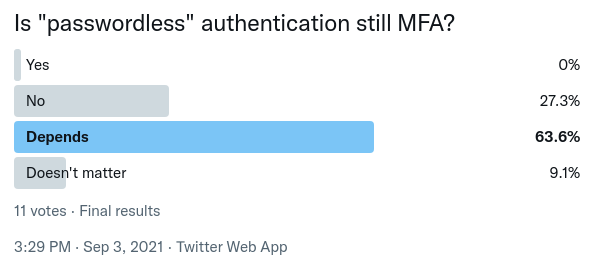
So here, over 27% think passwordless is not MFA. The vast majority clearly sit on the fence with depends with a whopping 0% believe it not be MFA. That is a pretty startling response.
I think there are probably a few things playing a part here. Clearly, this was not a thorough analysis – more an anecdotal discussion. However, passwordless is often marketed as cutting edge technology – and in many respects that is certainly the case. The use of modern cryptography, blockchain and advanced biometrics are all relatively new capabilities. As such, suppliers like to position themselves differently and uniquely to the market and their competitors.
To that end, they may see MFA as being existing and legacy – whereas the buy side see MFA as now becoming the standard operating model, with a level of security, business case evaluation and funding that allows roll-outs to be more easily accepted by senior business leaders. Any technology that doesn’t therefor fit into an existing model of comprehension, may well be seen as less secure or perhaps too difficult to compartmentalise and catergorise.
Passwords are dead, long live the password. However, passwordless technologies are still only starting to be adopted for both workforce and consumer identity projects. Terminology and design patterns may well need to leverage existing concepts to help drive understanding and adoption.
About The Author

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. He is also a part-time postgraduate on the GCHQ certified MSc. Information Security at Royal Holloway University, UK. His 2021 research diary focuses upon “How To Kill The Password”, “Next Generation Authorization Technology” and “How IAM Countermeasures Can Defend Against Cyberwar”. For further information see here.
