Introducing our Identity Security Scorecard
Our Identity Security Scorecard is a vendor-independent way of analysing your organisational capabilities with respect to keeping your Identity and Access Management infrastructure secure.
Assess
Understand your current maturity and identity security gaps
Analyse
End to end coverage of the key aspects of identity security for B2E, B2C and NHI.
recommend
Identify recommendations with respect to security, controls selection, usage and design
sustain
Support a strategic review and implementation that is sustainable
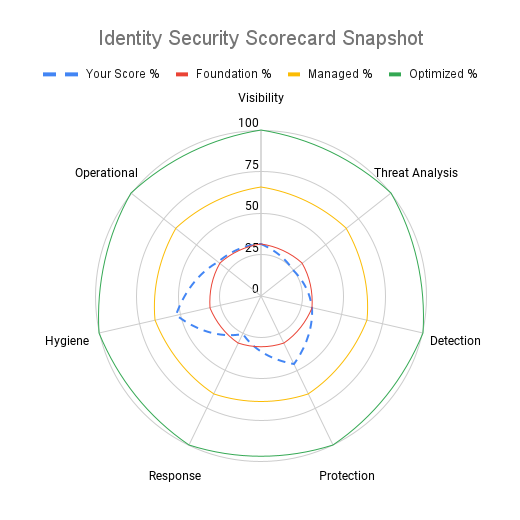
Visibility
Do you know where your identities are located? Who uses them? What systems do they access?
Threat Analysis
Can you perform continuous risk and threat analysis of your IAM components?
Detection
Can you detect runtime behaviour issues or mis-configuration within your identity data?
Our IDSS looks at 7 key areas
Identity security is not simply about selecting MFA or improving your PAM and IGA tooling. It must encompass an end to end view of identity data, behaviour analysis and operations.
Protection
Are you applying core IAM controls such as MFA, ZSP, JIT and credential rotation?
Response
Breaches happen – can you respond effectively and efficiently – incorporating the right systems and teams?
Data Hygiene
Are you removing redundant identities, permissions and policies?
IAM empowers your cyber teams. Improves employee productivity. Generates revenue. Don’t let the bad guys ruin it.
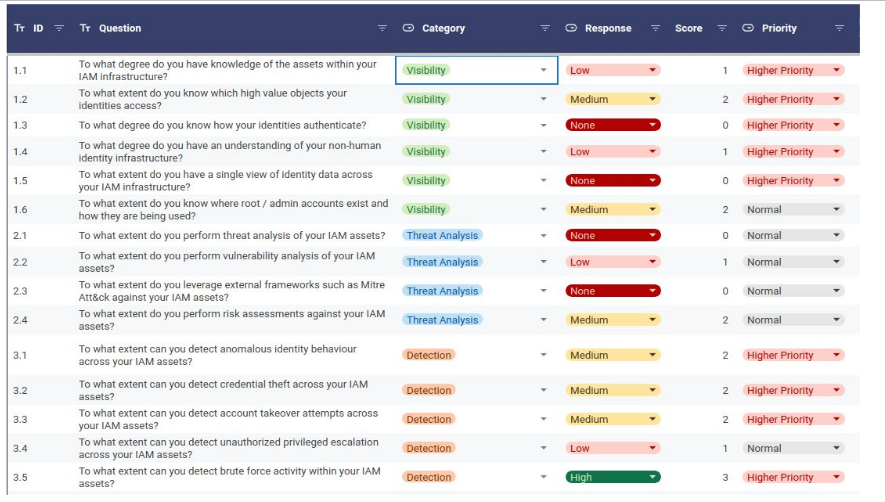
Identity Security Scorecard Assessment
IDSS: The Process
The Cyber Hut can be engaged to help your organisation identify risk, improve security, engage vendors and improve your overall identity security health.
