A few interesting items to hit The Cyber Hut intelligence inboxes over the past couple of […]
A selection of curated links relating to user login and authentication security controls and threat counter measures.
A few items to appear in The Cyber Hut intelligence inboxes this week. Styra Launches Cloud […]
Some items that have hit The Cyber Hut intelligence inboxes this week. State of Passwordless Authentication […]
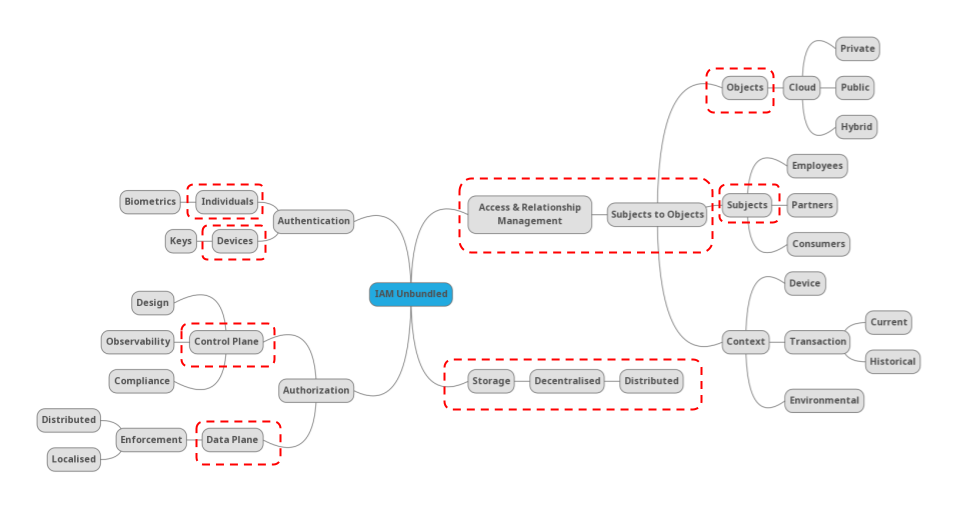
Identity and Access Management has long been confined to two (or maybe three) buckets: B2E (employee […]
On January 26th, the US Government issued a memorandum, relating to the adoption of zero trust […]
A few items that have popped into The Cyber Hut inboxes over the past week relating […]
A few items that have popped into The Cyber Hut inboxes over the past couple weeks […]
Identity and Access Management is going through a new golden age. The movement to IAM as […]