This week I wrote a guest article for Breez Security discussing the need for and evolution […]
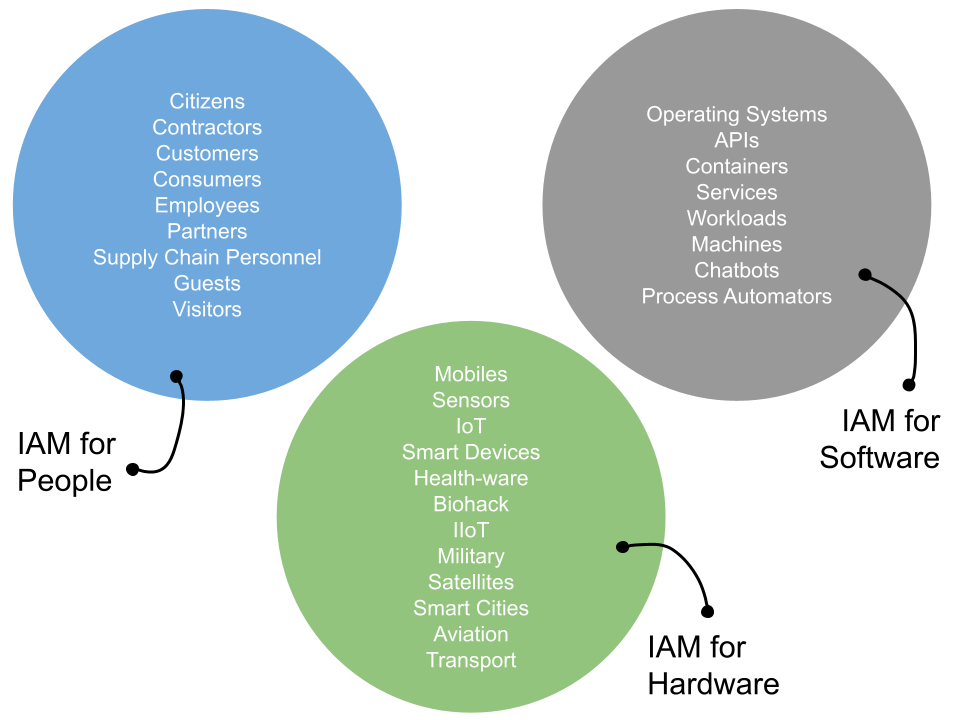
Trust is an omnipresent concept in the B2E, B2C and non-human identity worlds – where the […]
Some concepts to assist with improving security of an identity and access management fabric.
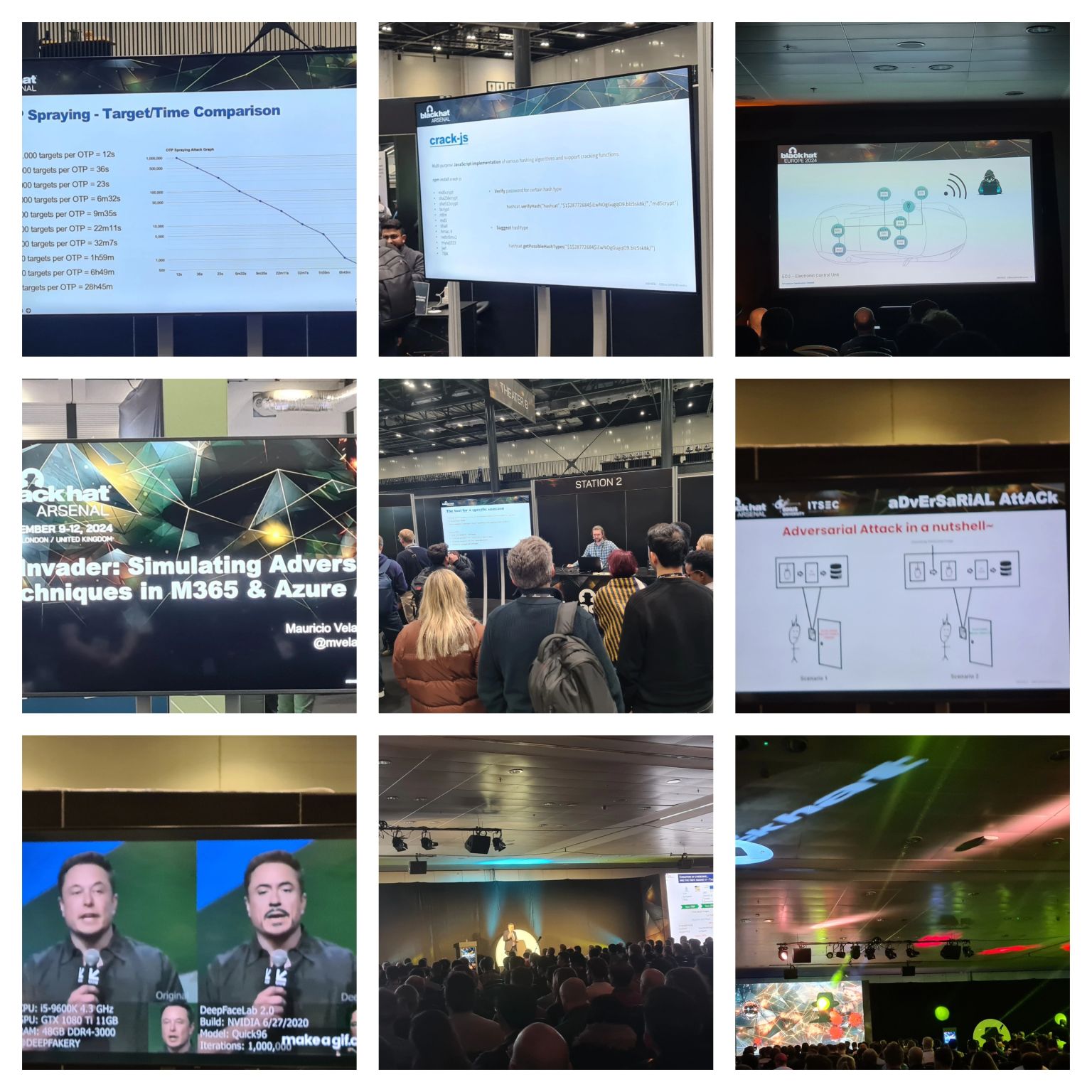
A review of some interesting briefings and tools found at Blackhat EMEA 2024.
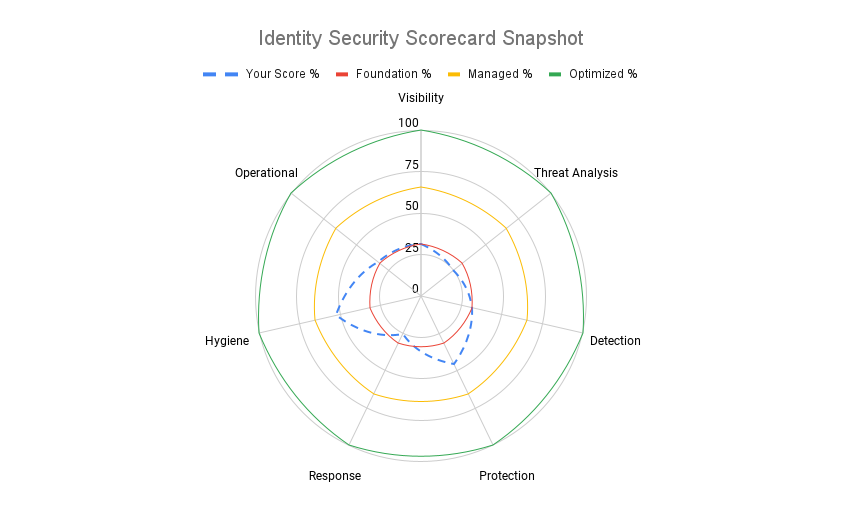
Identity Security is a topic we have tracked and discussed on numerous occasions at The Cyber […]
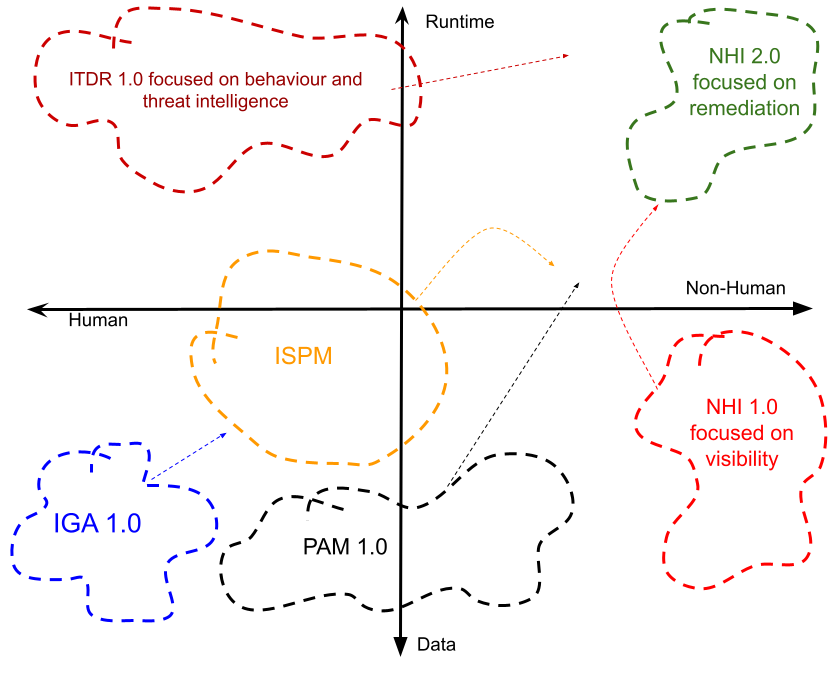
Identity Security – a complex, nuanced and yet equally dynamic, exciting and business enabling concept that […]
A discussion on the need to consider identity management as a set of life cycles - for expansion into the workload and NHI spaces.
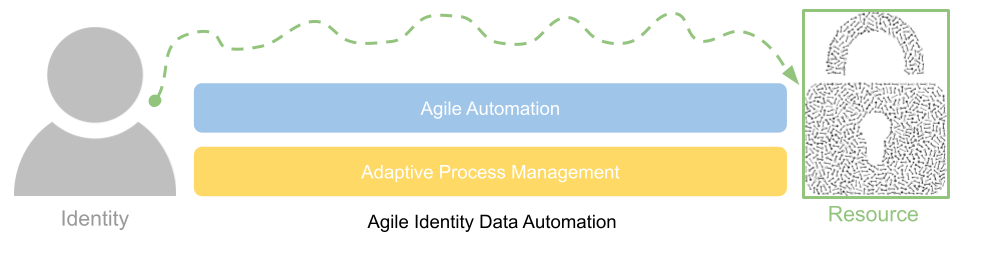
A discussion on why existing IGA projects are often in distress and how a more agile data automation approach can streamline process and improve application connectivity.
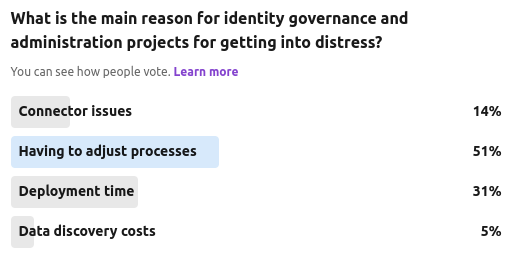
A discussion on modern identity governance and administration requirements and why many projects are in distress.
Our latest community poll was focused on the ever growing murmur that many privileged access management (PAM) and identity governance and administration (IGA) capabilities are either starting to overlap, or dedicated solution providers from each world are starting to add in "lite" functions from each others feature set.