On January 26th, the US Government issued a memorandum, relating to the adoption of zero trust […]
Identity and Access Management is going through a new golden age. The movement to IAM as […]
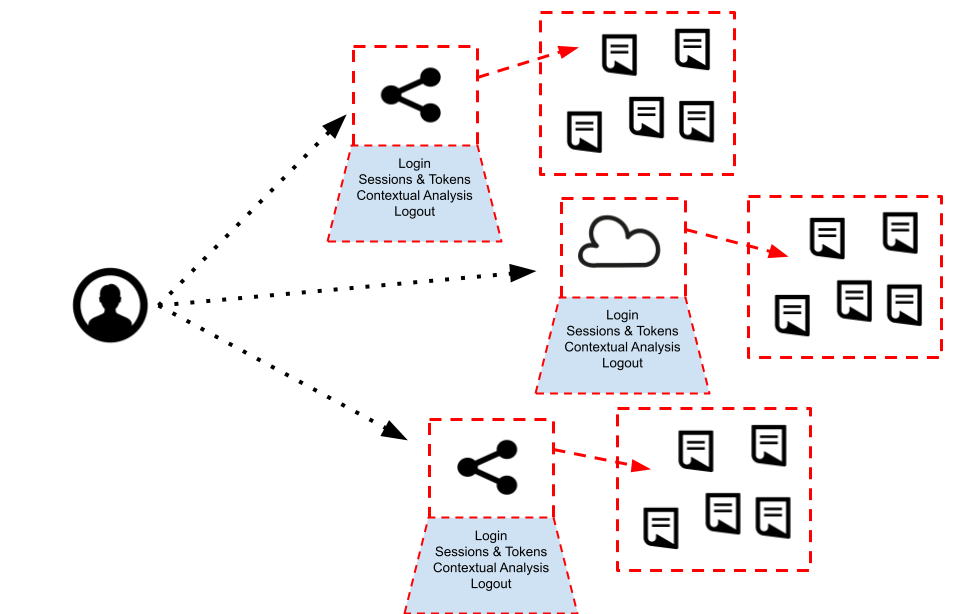
Customer, consumer and citizen identity and access management platforms are often plagued by the internal design […]
Note the subtle play on words there? Is cyber security a huge mess of complexity or […]
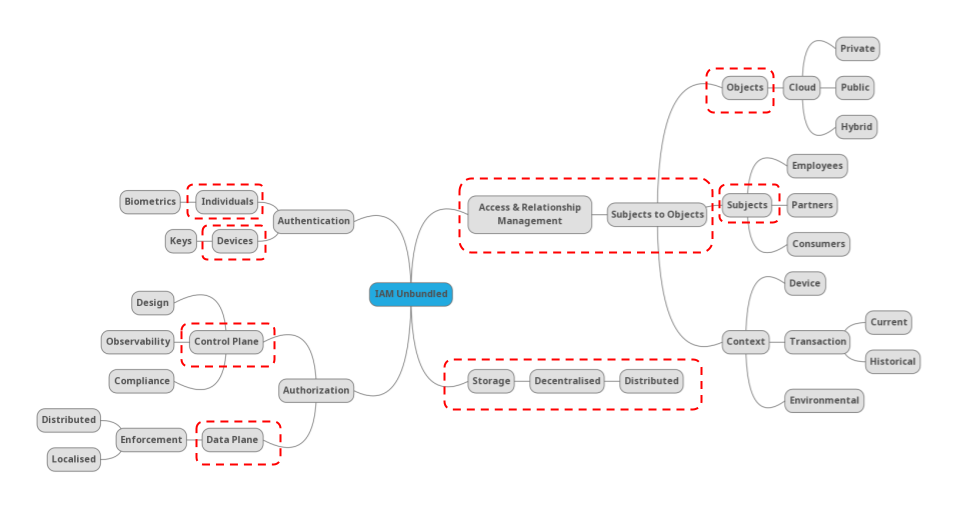
Authorization – the old chestnut often associated with role based access control – is seemingly making […]
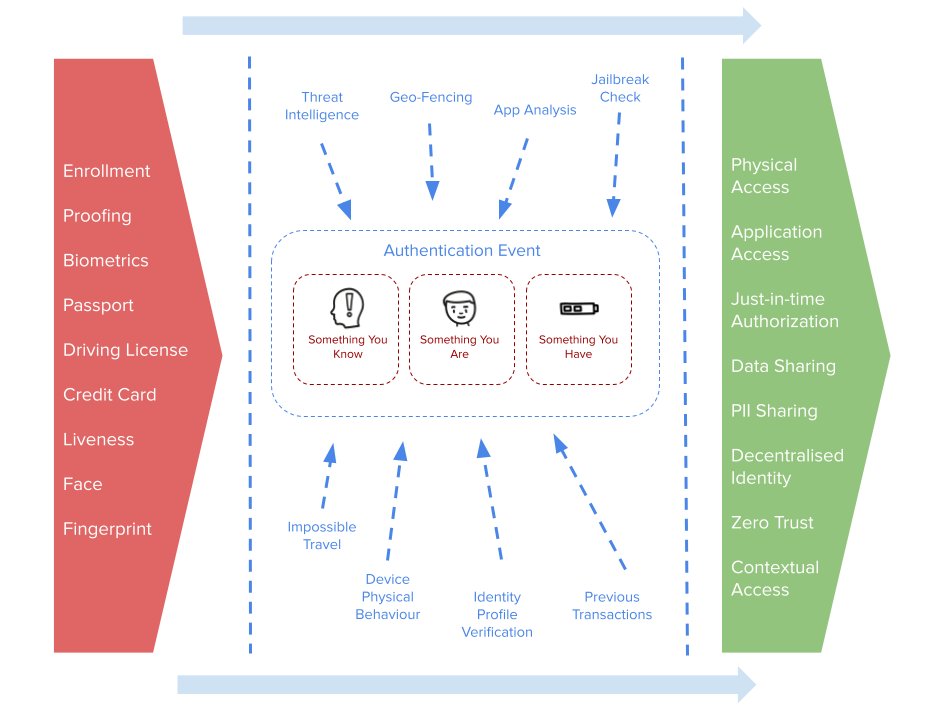
Authentication does not exist in a vacuum. It does not exist in a silo. The aim […]
I recently ran another of my highly scientific polls on cyber security technology opinions last week […]
Let us start with a few definitions just to get started. Authentication is focused upon asserting […]
This week two European software as a service consumer identity and access management (CIAM) vendors merged to what is claimed to be Europe's largest CIAM supplier.
iWelcome and Onegini become one, with the aptly titled new organisation called OneWelcome. Both have been long time suppliers of CIAM capabilities to primarily the European market.