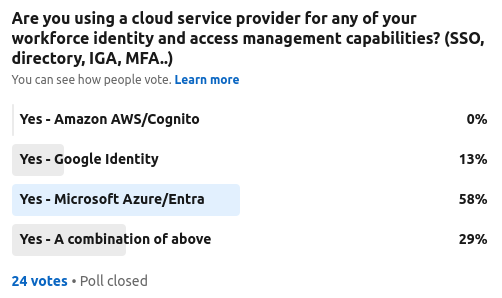
A review of the recent re-brand of Microsoft Entra for their IAM capabilities and the results of two community polls relating to Microsoft adoption.
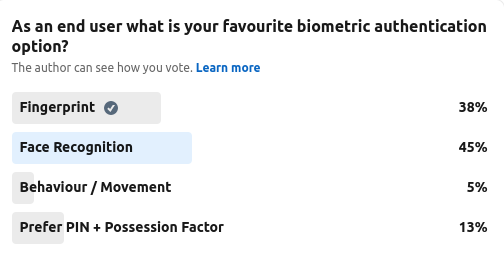
As part of The Cyber Hut's anecdotal community polls, we asked as an end user, what is your favourite biometric authentication option? The rise of device specific biometry to unlock our Android and iPhone based devices has increased in the last 3 years and many smart phone users will chose this over a basic PIN (albeit PIN is likely still needed after a hard reset).
I'm proud to announce today, the latest addition to The Cyber Hut online and in-person identity and access management training courses: Authentication Design & Management.
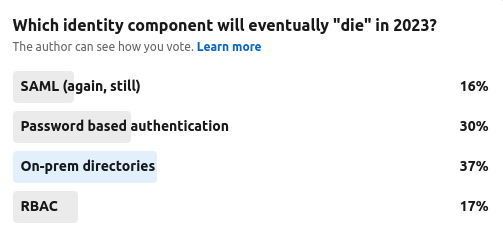
Each year a particular standard, component, model or approach within the identity and access management will be declared "dead" by expert commentators, startup vendors or just the bloke in the pub. As part of The Cyber Hut's Tuesday polls, I decided to test the water on this highly emotive topic before the Christmas holidays for our last poll of 2022.
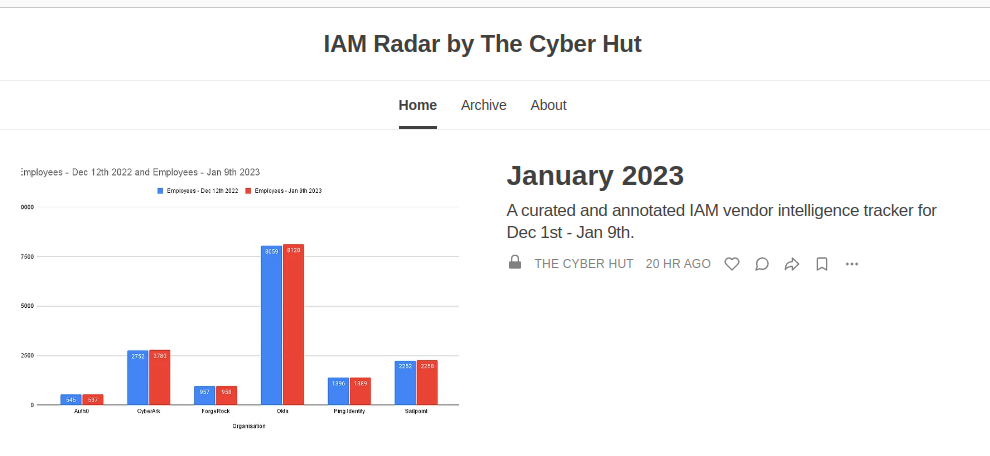
Today I'm proud to announce the launch of The Cyber Hut's IAM Radar: a subscription based curated vendor intelligence report. Released monthly, the report tracks the top 6 vendors in the global identity and access management space, providing insight, impartial comment and analysis to empower those within industry, consultancy, vendor and investment communities.
I wanted to wrap up 2022, with an anecdotal look at some of the key facts and figures that made up the bulk of The Cyber Hut's interactions, research and community engagement over the past year.
It has been a great year professionally and personally, yet parts of the world are still being ravaged by the pandemic, conflict, economic turmoil and the cost of living crisis. Hopefully 2023 can start to stabilise some of those broader problems we will undoubtedly all feel in the coming months.
I want to take a retrospective look back at 2022 in numbers, adding in a few stories and comments as I go. I hope you enjoy it and thank you to all of the global identity and access management community who have engaged with The Cyber Hut over the past 12 months.
Two weeks ago we ran another of our LinkedIn polls, querying the cyber, identity and access management community around a perennial question the industry has yet to consistently provide an answer for - in both user behaviour and technical solutions - "would you pay for privacy?".
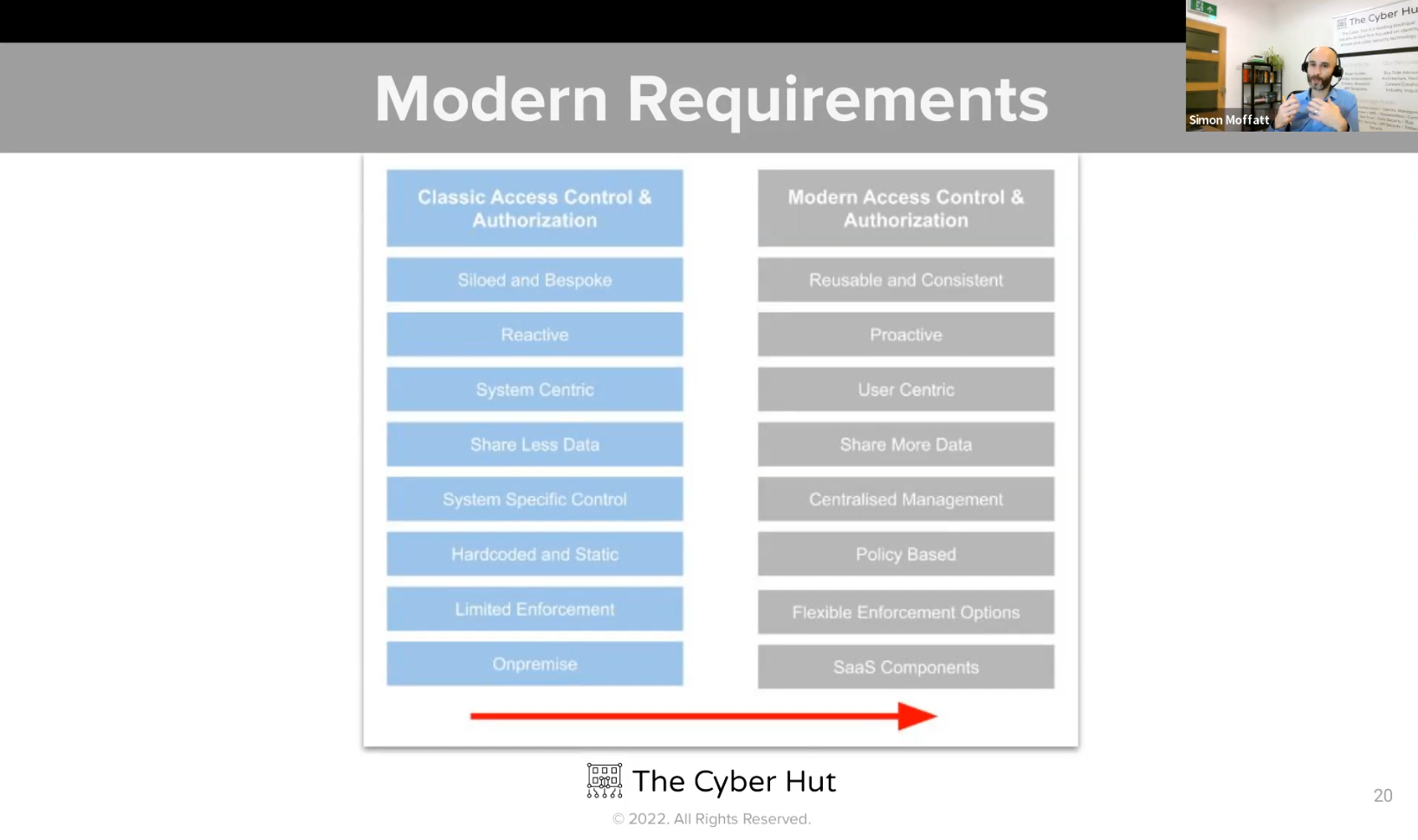
Zero Trust has been with us for the best part of a decade - since the likes of the Jericho Forum, Google's Beyond Corp and ex-Forrester analyst John Kindervag have all promoted a view of moving the concept of "trust" from a location to a concept based on the identity, device and associated context.
Version 2.0 of the US Department of Defence Zero Trust Reference Architecture has been cleared for public release and is a good, detailed read regarding an actual migration and implementation model. The document is available here.
An introduction to just in time, next generation authorization vendor sgnl.ai
Homegrown access control is limiting business agility - the ability to share data with those who need it, engage in joint ventures and B2B partnerships, protect PII and open up APIs to employees and customers alike. As such the market for authorization has increased substantially in the last 36 months. Funding rounds for the likes of Styra, PlainID and SGNL to name but a few indicate increased venture expectation that access control has a long tale of growth.