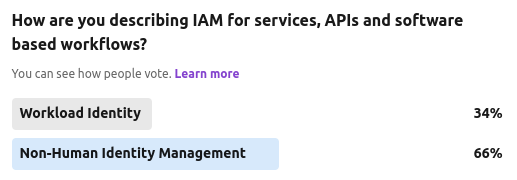
We ran another anecdotal community poll recently, asking whether this area of service IAM should be termed as "workload identity" or the more emerging "non-human identity".
The Cyber Hut recently ran a 7 day community poll on LinkedIn asking which of four big-ticket items will organisations be looking at from an identity and access management point of view.
So in this respect how does a workload differ from a machine? Well machines will typically be host centric and operating system related. That could be anything from bare metal servers (remember those?) right through to more specific devices working in the IoT, industrial IoT, aviation, transport or medical spaces....
This four-day security extravaganza tours the world, and I attended the keynotes and briefings sessions on the 6th and 7th. Clearly this is a broader security conference, but as always the role of identity and access management appears in more ways than previous and often in slightly less obvious ways.
Machines are eating the world. Or is it software? No wait, it's AI. In someways, it will likely be none, neither or all. I don't think any will make us all extinct, yet automation, the use of machines and services (powered by clever software) will certainly be doing more for us as humans than ever before - as employees, customers and citizens.
In light of the recent integration of ForgeRock into Ping Identity, The Cyber Hut has received numerous inquiry calls regarding potential integrations, feature overlap, next steps and existing deployment advice. To that end, we're making available a basic feature comparison matrix that highlights the basic capabilities each vendor as in each of the main identity areas of B2E and B2C. This matrix was compiled using publicly available references with peer review by those who have implemented ForgeRock or Ping technologies in the last 3 years.
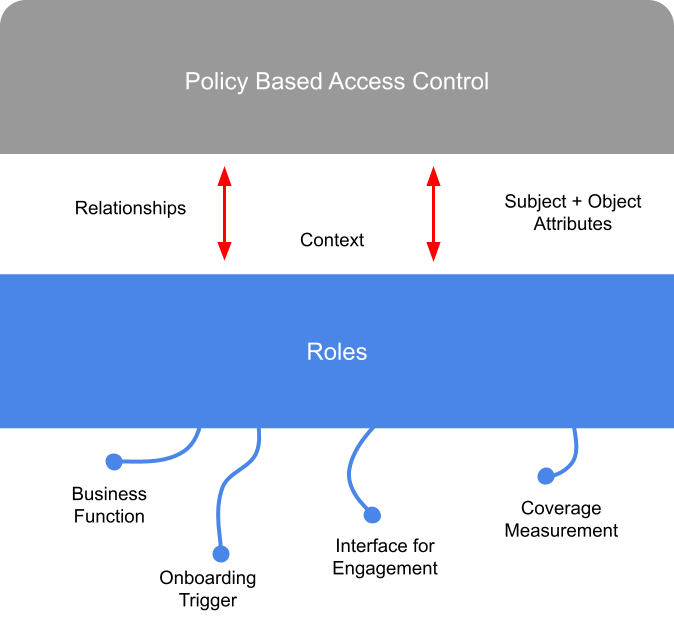
A discussion on how role based access control may still deliver business value, if deployed in a slightly different way.
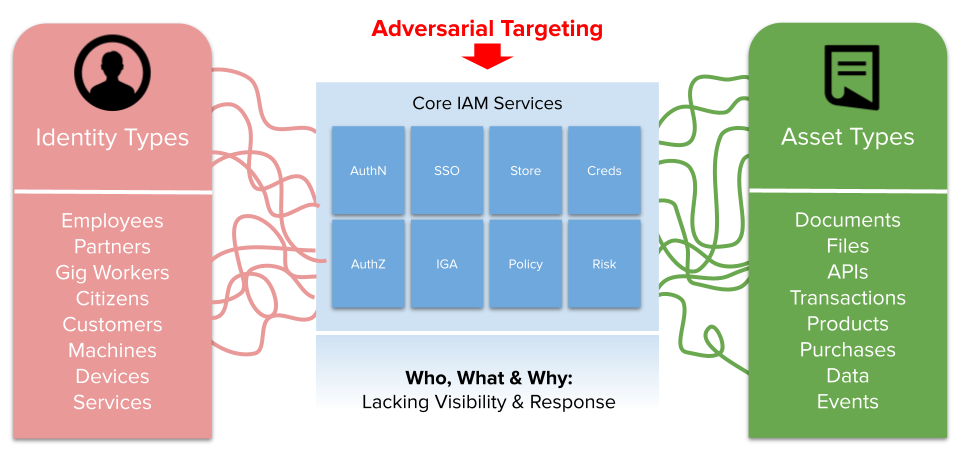
I wanted to expand to this based on conversations I've had over past 4-5 months as part of a research report coming out soon from The Cyber Hut on ITDR - what it is and why it's important now. The last thing I want to do however, is create more confusion and definitions! In order to avoid that I want to break down the term bit by bit.
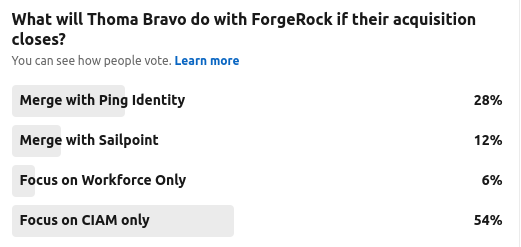
An opinion piece analysing the potential acquisition of ForgeRock by private equity firm Thoma Bravo.
Last week I had the pleasure of presenting a rapid and remote 10 minute keynote at the southern LATAM IAM Tech Day Event.