Our latest community poll was focused on the ever growing murmur that many privileged access management (PAM) and identity governance and administration (IGA) capabilities are either starting to overlap, or dedicated solution providers from each world are starting to add in “lite” functions from each others feature set.

N=56 responded, with a pretty resounding 71% thinking that a consolidated offering is the destination for providers. There is quite a lot to unpick in this however – and as always, social polls are just one signal in the noise of analysis and trends.
Comments on the poll:
- “A user should only ever have a single identity – that identity can have multiple credentials – but they should only ever have a single identity. Users can own and manage service accounts but they should not be able to use it ‘as’ as service account persona.”
- “It all converges in the next 3 years!!”
- “You Betcha!”
- “Once you start exploring cloud infrastructure and entitlement management and cloud PAM, the distinction gets blurry very very quickly”
Current PAM Capabilities and Future Challenges
So PAM is clearly focused on those high risk service, shared and infrastructure related accounts used by infrastructure operations, server teams, IT security administration and latterly devops and continuous delivery teams. Controls delivered to these accounts do not cover all “standard” employee or customers. So the focus is narrow, the risk higher and the controls more complex.
Standard PAM Capabilities:
- Account Discovery – Ability to identify high risk accounts, permissions, shared accounts etc
- Session Management: Monitoring, recording, and controlling sessions initiated by privileged users
- Audit: Ensure actions can be audited and unauthorized activities can be detected and stopped
- Least Privilege Enforcement: Ensuring users have only the minimum level of access rights necessary to perform their job functions
- Multi–Factor Authentication (MFA): Requiring additional verification methods beyond just passwords to authenticate privileged users – or prior to assigning privileged permissions / checking out accounts
- Access Request Approval Workflows: Implementing controlled workflows for requesting and approving privileged access
- Access Policy Enforcement: Defining and enforcing policies that govern who can access what, when, and under what conditions, often based on roles within the organisation
In the modern enterprise, PAM (access management, identity management and account management for high risk accounts) becomes more complex. We see a highly distributed landscape firstly – with infrastructure, applications and services in different locations – from on-prem (virtual, containers), cloud service provider (CSP) delivered compute and storage power as well as pure SaaS delivered applications.
The rise of workloads, machines and non-human identity capabilities also add more demands on how this high risk ecosystem is managed.
Future Challenges:
- Hybrid locations for asset protection
- Rise of non-human identities, workloads, devops and security as code
Example vendors in this space include BeyondTrust, CyberArk, Delinea, Saviynt, Senhasegura
Current IGA Capabilities and Future Challenges
IGA is a sector that is at least 20 years old commercially – driven by financial services regulation, audit requirements and the never ending quest to answer the “who has access to what” – and why? The early incarnations (disclaimer I was part of Vaau (later Sun Role Manager, later Oracle Identity Analytics) that made huge strides forward in moving the process from being a purely consultative (and essentially long and expensive) process to something more repeatable and automated.
The interesting aspect being that many large (typically finance, pharma and healthcare) organisations will assign budget to this process every year – namely to avoid compliance fines (IGA software + services costs < compliance fine = win!). To that end, the IGA market has seen continual innovation over the past 20 years – with improved connectors, workflow generations, access review complexity reduction, entitlements discovery and so on. More latterly the emergence of AI to tackle the identity “big data” problem.
Standard IGA Capabilities:
- Identity Lifecycle Management: Manages the entire lifecycle of user identities from creation, through modification, to eventual deactivation – not all stages will be managed by an IGA tool, but the IGA will contribute to the management
- Access Governance: Ensures that users have appropriate access levels by enforcing policies and controls
- Role-Based Access Control (RBAC): Defines roles within the organization and assigns access rights based on those roles – this likely only contributes to the coarse grained model, with attribute and policy based access control providing more fine grained options
- Access Request and Approval Workflows: Provides a structured process for users to request access to resources and for managers or IT administrators to approve or deny those requests
- Compliance Management: Contribute to the reporting for regulatory requirements
- Self-Service Capabilities: Empowers users to perform certain tasks themselves, such as password resets and access requests
- Analytics: Offers comprehensive insight and analytics tools to monitor identity and access data, identify potential risks
Some major criticisms of IGA projects, often see the scope being reduced to the either the most “complex” systems (perhaps difficult to connect to or have complex permission relations) or those systems that have a specific compliance requirement. So we start to see IGA focusing on the “top 10%” of the system community, with many remaining systems sitting in a disconnected or ticket-only style way of managing access. Is that similar to how a PAM system would be deployed – focused and constrained?
Future Challenges:
- Integrating with a broader range of services
- Ability to be non-prescriptive with respect to business processes
- Analysis of vast amounts of entitlement and activity data – likely AI led
Example vendors in this space:, ConductorOne, ForgeRock, Omada, Oracle, RadiantLogic, Sailpoint, Saviynt, YouAttest
So can we start to see the overlap or even eventual convergence of both IGA and PAM tool-sets? A second piece of anecdotal research was a poll we asked the community back in 2023 on whether we should start to think about all standard employee and customer accounts as being privileged.
This poll was slightly closer but gives a good indication that many see standard identities and accounts as perhaps being high value targets for adversarial activity – maybe releasing PII or acting as a starting point for lateral movement.
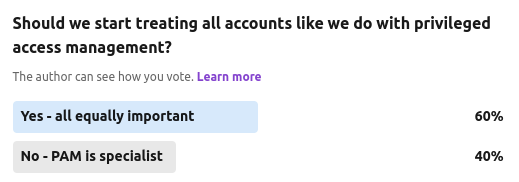
The counterpoint of course, is that if all accounts are privileged in their nature then none are – as the ability to identify relative risk (and in turn specific adaptive control counter measures) diminishes.
What empirical evidence do we see in industry of any initial overlapping approaches? Some examples include:
- Saviynt a leader in the Gartner Peer Insights for IGA, yet also deliver PAM for cloud capabilities
- Delinea acquires Authomize an ITDR vendor – whilst orthogonal, Authomize had security posture management capabilities and cloud infrastructure entitlements management features
- Next-generation IGA provider ConductorOne delivering features such as zero standing privileges, access fabric and CIEM
- Cloud SSO pioneer Okta delivering Okta Privileged Access for ZSP and unified IGA messaging
Of course, any continued and stable convergence will require a new term and acronym! I will leave that to the community…
Related Insight:
