This week I wrote a guest article for Breez Security discussing the need for and evolution to a more detective element in our identity security landscape.
Our the past two decades organisations and IAM related vendors have supported a model of security controls embedded within particular point solution spaces. Concepts such as MFA, credential vaulting, bot detection, co-pilot lead access review management and the like are all essential components of an overarching security architecture – but they are not enough.
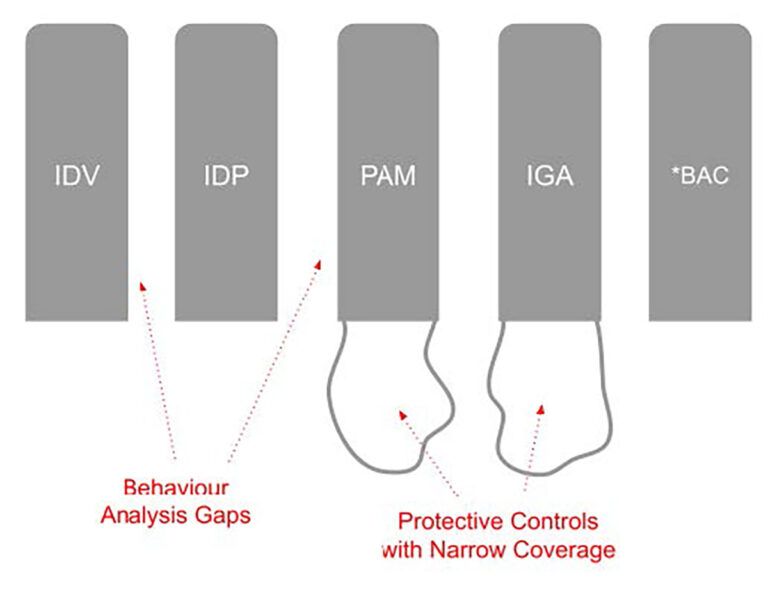
It is typical – and indeed common – to see weekly breach reports for large organisations who have already deployed mature IAM components such as MFA, PAM, IGA and connector systems – only to still be impacted by credential theft, privilege abuse, non-human identity issues or have been unable to reduce dwell times or have a clear picture of account usage.
Protective controls are often quite isolated in their deployment – focused at a resource level – and not necessarily being designed in an end to end information flow or access path way of thinking. The access path being the link between the subject and the downstream object they wish to access. To link those subjects to objects, we need an array of both identity, cloud, network and data security products and infrastructure – often spanning cloud and hybrid deployment landscapes.

By designing monitoring solutions that are focused on both the runtime behaviours of all our identities and have that cover a broad array of system integrations, we can start to move towards both better identity vulnerability discovery, as well as being better able to deploy response controls and countermeasures at runtime.
Read the article to know more.
