Identity Security – a complex, nuanced and yet equally dynamic, exciting and business enabling concept that has emerged in the last 3 years – yet still generates a great deal of inquiry discussion around what it is, what it isn’t, which vendors deliver it, what do they actually deliver and so on.
To that end, I thought it would be useful to put on paper a few truths around what Identity Security is and more importantly isn’t.
What It Isn’t
There are a lot of hours dedicated to discussions on what particular market sectors, acronyms and non-standards based terms actually refer to across an array of technology and scientific areas. Quite honestly it’s exhausting and not productive. Category creation, pioneers of particular segments, “owners” of capability sets and so on often just creates more confusion for the buy side – and the consultancy community too.
OK. So let’s do the opposite. Taking a note out of the excellent Psychology of Intelligence Analysis, let us work backwards. By that I mean let’s not find the burglar by looking for incriminating evidence that essentially helps fulfil our confirmation bias. Let’s remove from our list who isn’t the burglar – based on positive evidence and see what’s left.
So, what Identity Security isn’t. It’s a not a feature and it’s not a single product. It can’t be turned on or off like you would with an inline gateway, or an authentication factor on an identity provider. It is also unlikely to all come from a single vendor – meaning it likely isn’t a single platform.
How to come such a simple statement? A basic Crunchbase search for example generates over 70 organisations that have “identity security” in their description. Those 70+ vendors are not competing with each other. By that I would refer to the fact they likely deliver not only very different features, have more importantly from a competitive point of view, is that they have very different RACI matrix with respect to the three main personae that are touched during the procurement process – namely buyer, operator, implementator.
So if we have this thing that isn’t really a technology capability per-se, what are we talking about then? Why don’t we pick up the generic bucket named “concept”. Concepts are nice and broad – and cover the three main pillars that can actually support business change: people, process and technology. We must always remember, that cyber, identity and technology in general is there to support the business. There is no business? Well you probably won’t need MFA or vaulting, or that fancy homomorphic encryption platform.
Nearly all successful technology concepts need to integrate against a backdrop of process, measurement, culture and so on.
So if Identity Security is more a concept, what does that entail? Well absolutely we will need some software – either enhancing existing investments (this might not seem cool, but is actually highly cost effective, prudent and delivers value, see architecture review for that) as well as augmenting what we may have with some new tools. The second aspect is more around the people who will use software related to Identity Security, what they will do, what success looks like for them and what processes need to be created, removed and altered in order to support that success model.
Similarities to Zero Trust
Before I go on to explain more about the nuance of Identity Security holistically, let us quickly divert to another confusing 15-year overnight buzzword success that is zero trust. I won’t explain what that is (or isn’t) you have Google too. Be assured tho, that it is a process not a product and requires structural change to how we think about network, data, endpoint and identity-centric security. These changes require the trifecta of people, process and technology. Which is why many organisations are still “migrating” to it, with every vendor at every conference supporting this journey. Alas they too will need more than just technology…
End to End Life-cycles
So back to trying to understand more specifically what identity security is. I want to just take a step back firstly and get us thinking about life–cycles as they pertain to identity and access management (IAM) in general. I wrote a detailed view on the need for life-cycling thinking about identity here. In short take three main buckets we need to provide IAM services for: people, hardware and software. Under each of those buckets, we will have numerous smaller subtly different buckets with different functional and non–functional requirements.
Either way, think in turns of creation, usage, change and removal. Each with triggers, events, sub-routines and integration points. Many initial IAM products would be isolated with respect to usage, capabilities and success metrics. Think for example of identity governance and administration – operating in a silo, tied to compliance as a trigger, integrated against specific applications for risk reduction and operated with incentives driven by regulation. IGA would be seen as a vertical integration pathway – going narrow with varying levels of depth. Similar stories would be applied to things like strong authentication or federation.
So a basic life-cycle for B2E identity could look something like the following:
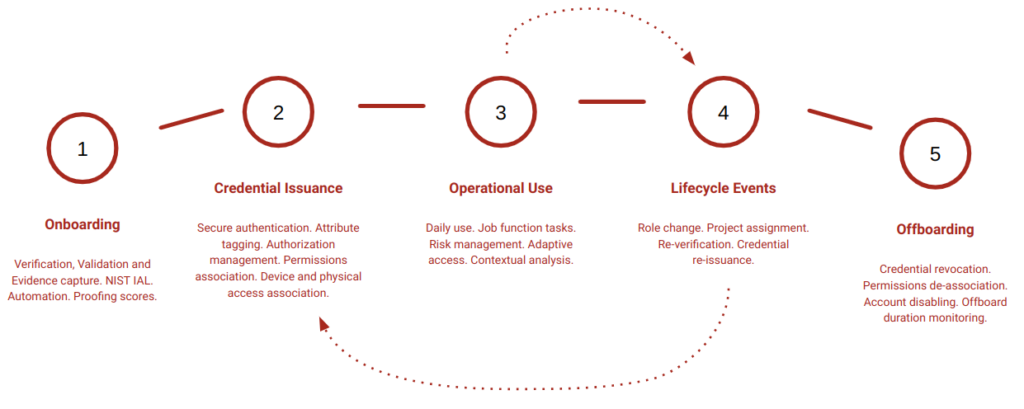
I’ve kept this B2E flow simple – but essentially it has has start, is quite prescriptive with respect to data schema, known changes and change requests and a documented off-boarding process. Life-cycles for consumers and non-human identities for example will be different and potentially more complex – the idea is to think about information flows, journeys and the link between subjects, objects and actions and all the intermediary people, processes and technologies needed to make that work.
7 Categories
So we have life-cycles and we will have different life-cycles for our different identity types. Next I want to overlay with some concepts of what Identity Security needs to deliver. I will introduce 7 high level categories labelled as: Visibility, Risk and Threat, Detection, Protection, Response, Hygiene and Operations. The eager eyed amongst you, will see that this resembles pretty much the NIST Cyber Security Framework. I have also added in specifically the hygiene aspect and operations.
Hygiene is really the advancement of IGA suppliers moving to use concepts such as Identity Security Posture Management – cleaning up persistent aspects of the identity journey. Profiles, permissions and also policy. Using known signatures, best practices and controls to essentially reduce the attack surface as it pertains to poor data management.
A comment on visibility too. The age-old cliche being “you can’t protect what you can’t see”. Or “you can’t stop what you can’t see…”. Either way, to design an effective risk management process, which covers assessment of the likelihood and impact of particular threats, you first need to understand your IAM landscape. Components, people, roles, responsibilities, data and also runtime integration aspects. It is still a huge issue for many organisations due to the traditionally isolated nature of IAM components as well as the hybrid deployment model too – with containers, on-prem, SaaS and CSP delivered aspects too.
So what next? Well The work of The Cyber Hut’s Identity Security Scorecard, which contains over 50 different areas of investigation to help organisations understand their maturity, risk exposure and architecture priorities, can be used to overlay these 7 categories across the IAM life cycles.
A concrete example could be to think of visibility in terms of a B2E life cycle.
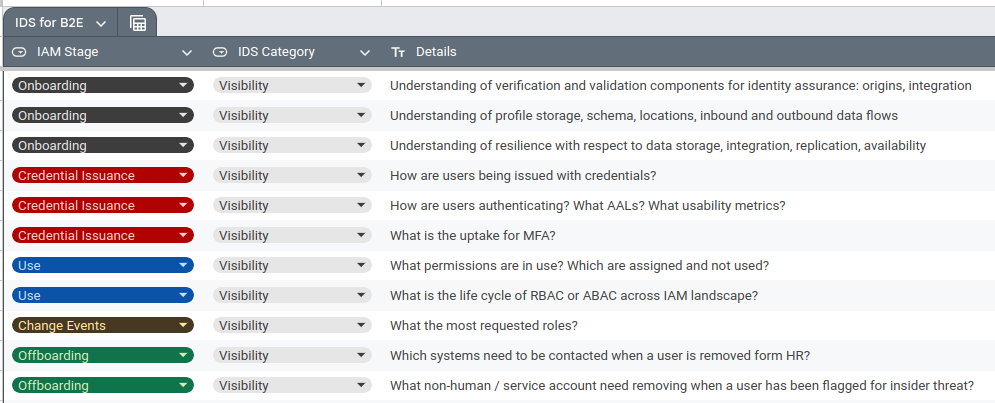
The above is a very small subset, but you can instantly see we’re touching different flows, systems and accountable owners. Detection stages would be just as broad, as too would Protective controls that touch upon authentication, authorization, token issuance, session management, segmentation and so on. These matrices become very large, very fast.
Which amplifies the point that Identity Security is not a one-size-fits-all product or magic bullet tool.
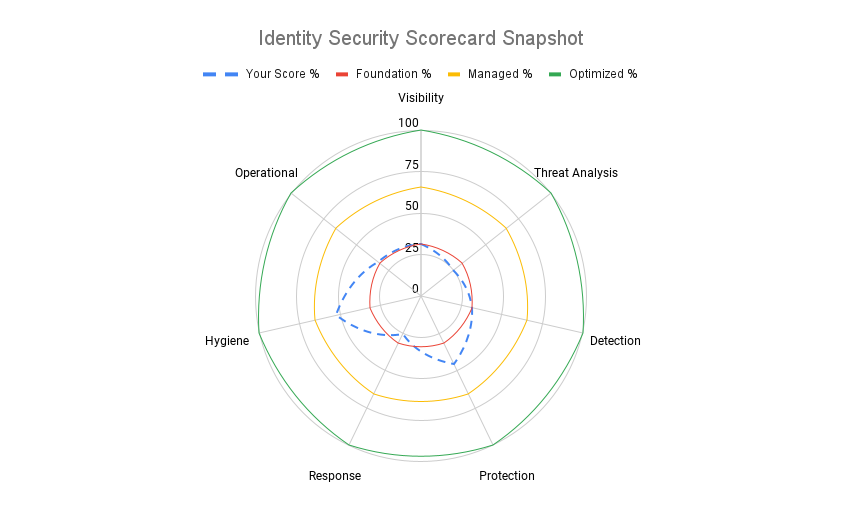
We need to consider that we have to secure the IAM infrastructure from the outside–in, as well as protecting it from the inside–out. We need both.
In Summary
Identity Security is a thing. We have lots of vendors delivering some amazing features covering things such as :
- Runtime analytics of access paths over-layed with real time cyber threat intelligence
- Segmentation of workload authentication
- Co-pilot focused access removal management
- Agent-less scanning of systems to identify all high risk accounts and permissions
- Automated controls generation tools and continuous monitoring
Note none of the above compete with one another – again indicating we’re looking at an holistic set of capabilities.
In our perimeter-less world, all data and cyber components will resolve on one base note: identity. Identity becomes an instantly attractive attack vector that needs managing both from the inside and the outside, with a heavy reliance on changing how we measure, monitor and maintain our identity operations.
About The Author

Simon Moffatt is 20+ year veteran of the IAM space. A published author, regular keynote speaker, podcast host and strategic advisor to a range of public and private sector entities on emerging identity technology. He is a Fellow of the Chartered Institute of Information Security, holds a Post Graduate Diploma in Information Security and has been a CISSP since 2007. He is currently writing IAM at 2034: A Future Guide to Identity Security. He is the creator of the Identity Security Scorecard.
