This week I hosted our most recent CISO briefing, taking a look into the world of next generation authorization.
Homegrown access control is limiting business agility – the ability to share data with those who need it, engage in joint ventures and B2B partnerships, protect PII and open up APIs to employees and customers alike. As such the market for authorization has increased substantially in the last 36 months. Funding rounds for the likes of Styra, PlainID and SGNL to name but a few indicate increased venture expectation that access control has a long tale of growth.
The breadth and depth of assets that the modern organisation needs to protect is becoming overwhelming for legacy solutions, as is the size and variety of the users needing access – from employees, contractors, customers and service accounts alike.
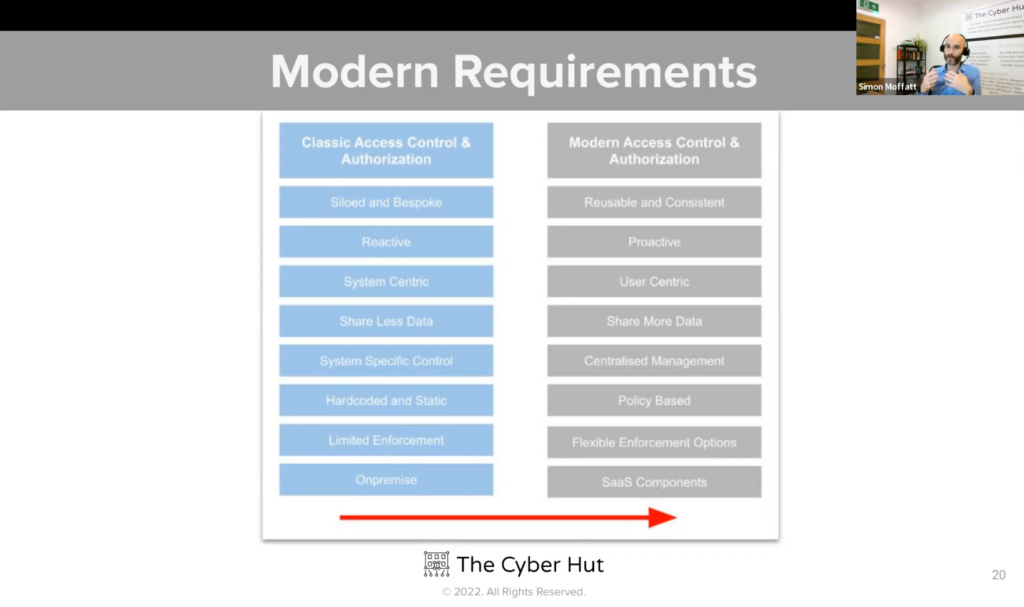
Concepts such as identity centric security – where identity and access management plays a foundational role in support of zero trust and distributed remote access solutions is also becoming more standardised within the CISO and CIO architecture plans for 2022 and beyond.
The webinar went on a journey to cover the back story of authorization, where we are today, a landscape industry review (looking at external authorization platforms, declarative authorization, access request management and existing access management platforms) before taking a look as to where authorization maybe heading for the next 36 months.

Watch again on demand.
Further Authorization Related Support:
CISO Authorization Advisory Services
Authorization Architecture Review
Open Source Signals Tracker for External Authorization (Eg Axiomatics, PlainID, SGNL, Scaled Access Veza)
Open Source Signals Tracker for Declarative Authorization (Eg Aserto, Cerbos, DataWiza, oso, Permit.io, Styra)
