Identity and Access Management is going through a new golden age. The movement to IAM as a foundational tool for B2E security and B2C business enablement is quite well known. The vendor narrative, funding and growth in both sectors is well documented. However, we’re also starting to see identity functions proliferate in a range of orthogonal technology areas. What about device security and IoT enablement? What about modern data security at both the “little data” and “big data” focus points? Aviation, automotive and rail all now rely heavily on identity at both the individual and non-person entity level. Are existing architectures able to deliver value across such a diverse range of use cases and integration points?
Identity and access management emerged in the employee space – where operational efficiency, productivity and connectivity where big measures of success. “If you connect system X to HR, we can provision a new contractor in 70% less time”. That is a nice tangible and more importantly measurable state of affairs that allowed B2E systems to proliferate. Secondary drivers such as regulatory compliance helped shift huge budgets to governance, provisioning and access control systems throughout the 2000’s.
The Platform Advantage
A platform advantage started to take hold as specialist point systems for access control, single sign on, provisioning, workflow, access request management and role mining all needed to communicate with each other. Standards helped, but organisations where spending vast sums on application workflow redesign and integration. Expensive stuff, which allowed platforms – capable of providing a range of horizontal capabilities – to flourish.
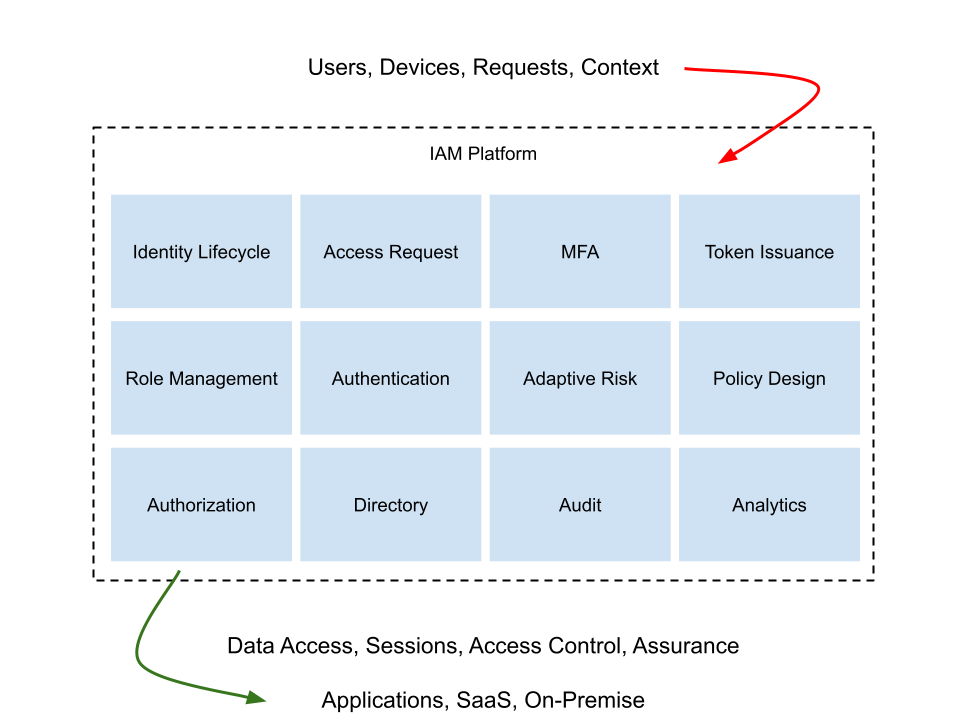
The platform play provided several advantages, as it was based on several assumptions. Firstly the output of the platform – namely assurance at the identity and authentication layers (see NIST 800-63 for some detail on those terms) – was being passed into a relatively controlled set of services. Controlled in the sense they belonged to an enterprise, perhaps at times with a bit of federated control in there too. But ultimately the applications where relatively static – in activity and growth terms. The IAM services would be owned by an IT operational team that measured its success against spend and productivity. Perhaps in more mature environments, security and usability metrics might also apply too.
But like all systems of complexity – remember the Altavista home page? – an unbundling approach can provide competitive disruption.
Bigger Wins Until It Doesn’t
Platform capabilities typically focus on incremental improvements to a solution. Horizontal expansion of features and vertical reach of integration. This helps leverage the benefit of investment by both a vendor and their customer base. A vendor will wish to consolidate its market position, likely by organic or perhaps market absorption of features at the edge of its core. So we started to see access request systems adding in role management functionality. Single sign on systems adding in adaptive risk. Vertical integration would come in the form of a range of SDKs, perhaps the addition of gateways and data security tooling which allowed the identity tentacles to reach further into downstream systems. This helped improve customer to vendor “stickiness” making it difficult to migrate.
However, there are some interesting developments, not necessarily on the solution side, but the problem side. The problems that identity now needs to solve are somewhat evolving and can’t necessarily be solved by incrementally innovating at the edge of a platform.
New Problems, Trump New Solutions
Innovation in delivery really comes from the emerging problem – rarely from making an existing solution faster, stronger or longer. Think cars versus faster horses. But what are the emerging pressures identity needs to solve? Clearly there are some pretty obvious meta trends: cloud first, mobile first, API first. That stuff is a given for many industries and technology types. As identity is now so pervasive, by association the output of any identity and access management capability requires broad coverage and applicability. OK, but what specifically in the cyber security and IAM spaces is occurring from a problem perspective?
We first probably need to understand a little more about who and what are going to consume IAM related capabilities. What problems do does those users of identity need to solve? We can bucket those service users into two camps – those from an outside–in perspective and those from an inside–out perspective.
The outside-in refers to systems, data and users not under the control of IAM services. The inside-out is the opposite. Systems, data and users that are under control. I am not really referring to control as in public network/private network – more in the sense of operational and budget control.
A patient requiring treatment by a doctor – this could be an example of an outside-in problem. An organisation allowing employees to work in a distributed manner with SaaS systems, could be an example of an inside-out problem.
Example Outside-in Problems
- Privacy preservation
- Digital empathy & loyalty
- Data usage transparency
Example Inside-out Problems
- Supply chain interdependence
- Response/recovery mechanisms
- Obverse-ability
Unbundling at the Edge
So we have some new problems and existing platforms of capabilities. But what of this unbundling aspect? Unbundling is typically referred to as a generic emergence of specialist capabilities, often driven by edge use cases and emerging “extreme requirements”. If we take the typical set of example IAM platform capabilities we can start to see innovation – in the form of venture capitalist funding, startup activity – in several of the main building blocks.
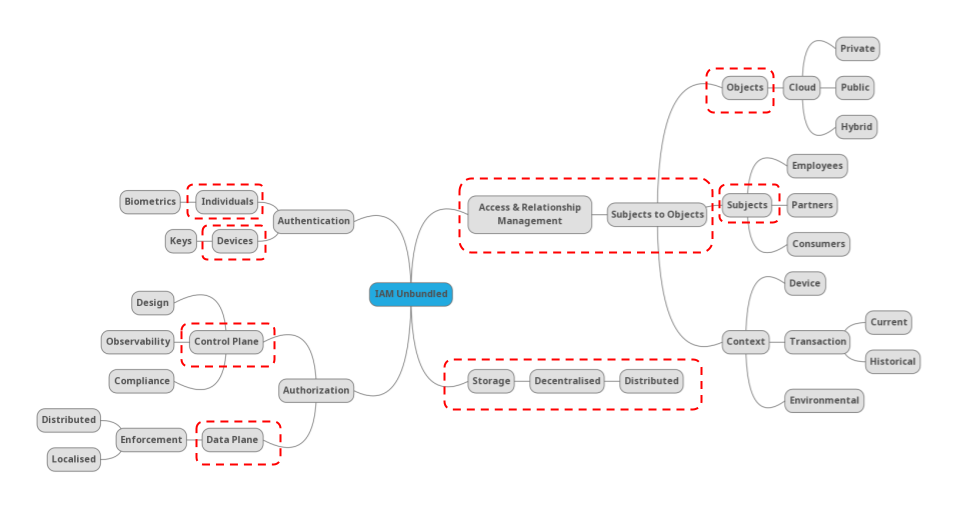
The above is just an example “mind-map” of emerging capabilities that a Google or Crunchbase search could reveal based on use cases and design patterns. The red overlay could indicate the debundling boundary, where more specialist capabilities start to emerge. What will make these boundaries more solid? Clearly repeatability and funding would help, but also an industry understanding of the some of the consistent non-functional meta patterns such as the requirements for autonomy, interoperability and generic evaluation which would help deliver privacy, security and recover-ability.
The aspect of recover-ability is very important. Unknowns are becoming the norm. A general lack of observability as it pertains to data, events, user behaviour and so on can make the impact of even minor disruption to be significant. A mechanism to overcome unknown outcomes or complex problems is agility – see microservices as an exemplar of that – and an ability to “fail fast”. Whilst that is important, the ability to respond and recover to system failure, high impact threats, competitive pressures, meta trends (aka the pandemic) will allow technology to play a leading part in competitive advantage.
IAM is now becoming so central in all business functions, that the ability for IAM related capabilities to recover from systemic failure, security threats, business direction changes and so on amplifies the benefits of a debundled set of capabilities.
In Summary
IAM is heading into a new golden age. The major meta patterns of zero trust, distributed working, complex supply chains and privacy preservation all rely heavily on being able to verify identities, their requests and the associated data in a distributed and autonomous fashion. Perhaps those capabilities can only be delivered in specialist yet highly interoperable pillars.
About The Author

Simon Moffatt is Founder & Analyst at The Cyber Hut. He is a published author with over 20 years experience within the cyber and identity and access management sectors. His most recent book, “Consumer Identity & Access Management: Design Fundamentals”, is available on Amazon. He is a CISSP, CCSP, CEH and CISA. He is also a part-time postgraduate on the GCHQ certified MSc. Information Security at Royal Holloway University, UK. His 2021 research diary focuses upon “How To Kill The Password”, “Next Generation Authorization Technology” and “How IAM Countermeasures Can Defend Against Cyberwar”.
